Expected results
The project will develop techniques, tools, and processes that support design techniques for evolution, testing, verification, re-configuration and local analysis of evolving software. The project results will be applied and evaluated in particular in the industrial application domains of mobile devices, digital homes, and large scale air traffic management which all offer both great research challenges and long-term business opportunities.
The project aims to progress beyond the state-of-the-art in the following research directions. Because configuration management can no longer be separated from the development of the application, one objective is a configuration management process that is tightly intertwined with the development and life-cycle processes defined in the project. This process will be supported by model-based tools that allow for automated reconfiguration as a reaction to change as well as verification of security properties in a changing context.
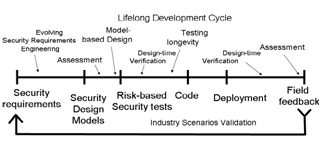
There is so far little work on analyzing models for adaptive security requirements, so one of the main scientific challenges of the project will be the construction of such an analysis approach and the associated tool-support. Another dimension in which the state-of-the-art will be improved on will arise from the link of the model level to the run-time execution of the system using model-based security monitor generation. The project will develop a model-based design approach that is tailored to the needs of the secure development of self-adaptable systems. The approach will glue requirements techniques with the final code and configuration and will provide tools that allow the user to automatically analyze the models against its a-priori requirements, also taking into account the configuration scenarios that the assessment analysis has defined likely. The project further has the goal of generalizing existing methods and techniques for security assessment to cope with longevity. This will address the issue of system documentation to facilitate assessment of security modulo changes. We will address the question of how verification is possible if the assumptions are going to change. Finally, we will define testing strategies highlighting the evolution or non-regression of the system wrt. traceability of security requirements.
Concrete achievements will include thus the following:
- An architectural blueprint and an integrated security process for lifelong adaptable systems that acts as a common framework for all the techniques and tools delivered in this project.
- A requirements engineering methodology that supports dealing with the fact that in long-living systems, both the requirements and the implemented systems will change after the initial development has finished.
- A security modeling notation for modeling adaptive security designs, together with formally founded automated security analysis tools.
- An IT security risk approach able to assess the evolution of risk profiles due to the evolution of either system or attacker model.
- Techniques and tools to verify adaptive security requirements when performing on-device software updates.
- A model-based testing approach that supports automated testing of evolving systems for security requirements.
The results are continuously validated jointly with key industry players.